3 min read
What is next-generation antivirus?
Published: April 12, 2022 Updated: April 10, 2024
While "next-generation" may sound new and revolutionary, next-generation antivirus actually has roots in technology most of us are already familiar with.
Traditional antivirus vs next-generation antivirus
Both traditional antivirus and next-generation antivirus fall under the umbrella of endpoint protection.
While the term "endpoint protection" may be unfamiliar to some, most understand the concept:
In the past we relied on traditional antivirus to protect our individual devices. But we now know that these programs are not enough to protect users from evolved security threats. The basics of managed security have gotten more demanding in recent years.Endpoint security, or endpoint protection, is the process of protecting user endpoints (desktop workstations, laptops, and mobile devices) from threats such as malware, ransomware, and zero-days.
—Source: SentinelOne
Traditional antivirus relies on signature-based detection to identify malicious files. "Signature-based" means that the antivirus program compares the contents of the scanned file to a database of known threats. If the file's contents match signatures within the database, the traditional antivirus identifies the threat and quarantines the file.
Antivirus databases are updated daily, sometimes seeing hundreds of thousands of additions in one refresh. That sounds like a lot of new threats every day, but keep this point in mind: That number includes only the new threats we know about. The number of new threats created on a daily basis is likely much higher.
Traditional antivirus can't identify a file as a threat if its database doesn't have record of the malicious signature. A threat actor needs only to change a few lines of code to enable a dangerous file to slip past the antivirus database. So the bar for creating a "new" virus is much lower than many realize.
It may help to think about the limitations of an antivirus database in terms of plagiarism. (Literature and computer files are both made up of words, after all.)
Plagiarism is the outright copying of someone else's written work. If a threat actor were to rename an existing malicious file but change the file name (or plagiarize), the antivirus database would recognize and quarantine the new file. But if the threat actor were to paraphrase (or attempt to reach the same means by using different code or commands), the antivirus program might overlook the new malicious file.
Next-generation antivirus covers the same bases and more
Next-generation antivirus is not a fundamentally new concept, but it is fundamentally more thorough than traditional antivirus.
Because traditional antivirus relies on an updated database, users will not have real-time protection if relying only on this legacy program. (This point also makes the case for end user security training.)
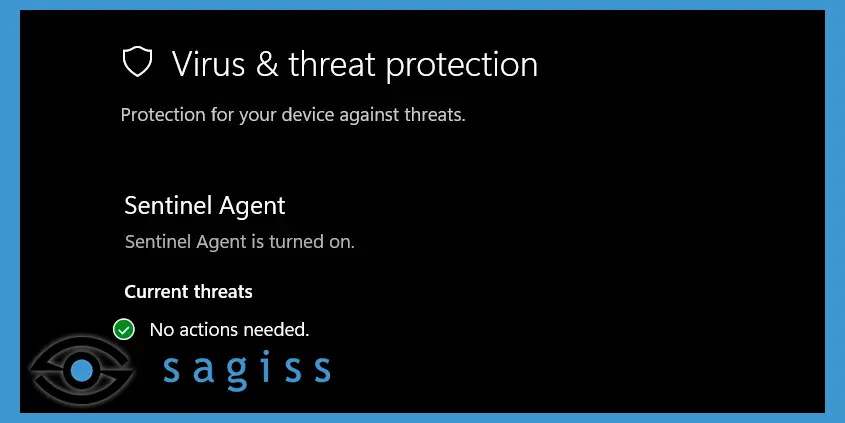
Next-generation antivirus is similar to traditional antivirus in that it includes a signature-based component. This means that next generation antivirus can provide the same protection as traditional antivirus even when your devices are offline.
Imagine that you're on a flight with no internet access. A potential client gave you a thumb drive featuring some files you need to review so that you can create an estimate for your services. Unfortunately, that thumb drive is infected with some sort of malware. Because next-generation antivirus installs an updated antivirus database on your system, you have the same level of protection as you would have with traditional antivirus.
The crippling limitation of traditional antivirus is that relying only on signature-based recognition means it can recognize malicious files only by their contents, not by their behavior.
Next-generation antivirus uses cloud-based artificial intelligence and machine learning to adapt evolving threatware and methodologies to offer security that traditional antivirus simply cannot compete with. So, next-generation antivirus can ensure real-time protection, as it always knows what activities to look for and flag as suspicious. Also, focusing on behavior rather than signature gives next-generation antivirus an advantage against polymorphic (self-editing) malware like emotet.
Also, traditional antivirus is useless against fileless attacks because there is no file to scan to identify threats in its contents. Identifying fileless attacks requires recognizing unusual or unwanted behavior, something traditional antivirus cannot do.
There's no need for traditional antivirus if you choose next-generation antivirus. Relying only on next-generation antivirus saves your company resources in a couple ways:
-
Computers need to run only one program, freeing up CPU and RAM and processing power on your individual machines.
-
Fewer software licenses mean you're not overpaying for protection.
Long gone are the days of installing an antivirus program onto your computer and going about your day.
As threat actors and their methods have become more sophisticated, so have our security needs. To keep up with the times, managed service providers have turned away from traditional antivirus programs and now instead rely upon next-generation antivirus tools to help keep their clients safe and secure.
 Jake LaCaze
Jake LaCaze